China’s Personal Information Protection Law (PIPL) went into effect on 1 November 2021. With its sweeping set of rules and regulations protecting the personal information of users, companies have to adapt quickly to ensure they remain on the right side of the law. Here are some of the core requirements of the law and some suggestions on how to build a robust IT system, which tools and technologies to use for assessing risks, and how to structure the organization to ensure compliance.
In this article, we explore concrete actions companies can take to comply with the Personal Information Protection Law (PIPL) currently in practice, mainly from a technical perspective.
Relationship Between Information Security, Personal Information Protection
As a rule of thumb, information security—a long-discussed topic in the IT industry—is the basis of personal information protection. Therefore, all security measures, whether technical or organizational, in the information security field are beneficial for personal information protection. Information security is the fundamental tool for personal information protection and is also an implied requirement of the PIPL. In other words, you cannot have good personal information protection without information security.
However, personal information protection has its own characteristics. Good information security doesn’t guarantee the protection of personal information, and well-placed security measures don’t mean personal information is being well-protected.
For example, you provide your mailing address, ID card, phone number, and other personal information to a commercial bank to apply for a debit card account. Commercial banks usually have strong information security, which means your personal information itself is secure inside the bank’s IT system. However, as is common practice, the commercial bank may occasionally want to send you an SMS promoting other investment tools, such as a fund or wealth investment product, especially during the few days when you have a large deposit in your debit card account.
This behavior is a clear violation of your privacy, since you only provided your personal information to open an account and may have no interest in the bank’s wealth investment service. However, the bank has changed its purpose for processing your personal information and uses it to send out annoying messages. Despite this violation, from an information security perspective, your personal information is still well protected by the bank and there has been no unauthorized access to the information.
In short, information security and personal information protection are intersected while information security is the basis of personal information protection (privacy), but just information security is not enough for privacy.
Information Flow, Data Mapping
When we talk about personal information protection, we first need to identify the target for protection, which means we need to answer the below questions:
- Who collects the data, in which way, from whom, and for what purpose?
- Which system is used to save personal data and in which format? Where is the physical location of the system?
- Who has access to the data and for what purpose?
- Is the data being shared with a third party and for what purpose, if any?
The above questions are critical for the company to understand the current situation and practices regarding personal information protection inside the organization. The answers will also form the basis for implementing further control measures to protect personal information. The best way to answer the above questions is to carry out data mapping or data flow mapping—the first step that we recommend taking when a company starts carrying out privacy management.
Today, there are several toolkits available for data mapping, but it’s also possible to use an Excel sheet to record the information, as shown in the table example.
Table Showing an Example of Data Mapping
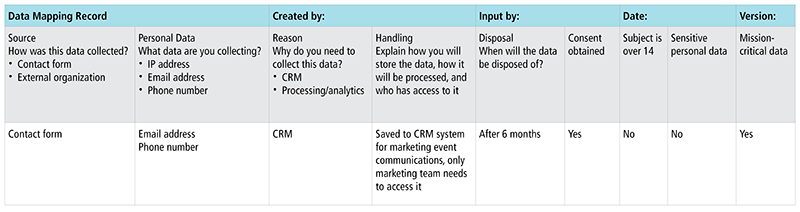
The key to effectively implementing control measures starts with a joint effort between the IT department and operations teams, or if possible, to have a personal data protection team as lead to identify the flow of personal information inside the organization and between external parties.
DPIA or Privacy Impact Assessment
Article 55 of the PIPL requests the company to carry out Data Protection Impact Assessment (DPIA) when “processing sensitive personal information, making automatic decision-making for the use of personal information, entrusting other parties to process the personal information, and providing personal information to overseas parties.” Article 56 further specifies the DPIA requirements, which should include assessing the purpose of personal information processing, the impact it may have on personal rights and interests, and whether the protection measures currently in place are adequate.
DPIA is also mandatory in most cases under the EU’s General Data Protection Regulation (GDRP), so it is likely already familiar terminology for most foreign companies. As a process for identifying the risk related to personal information, DPIA usually includes the following objectives:
- Identifying specific risks to personal data
- Analyzing how programs or systems collect, use, share, and maintain personal data to ensure compliance
- Determining the risks to personal data inherent in programs and systems
Once the DPIA process is completed, the below information should have been gained, and saved for at least three years as required by Article 56 of the PIPL:
- Description of the processing and its purpose
- The legitimate interests within the processing
- An assessment of the necessity and proportionality of the processing
- An assessment of the risks to individuals (or data subjects in the GDPR context)
- The measures envisaged to address the risks
- All the safeguards and security measures to demonstrate compliance
Many risk models have been developed in the past, and some are still popular and instructive for personal information protection in China. These include models such as the NIST Privacy Risk Model, Taxonomy of Privacy Problems, and the Compliance Model of GDPR/PIPL. Whichever model a company chooses, some common steps include the following:
- Identifying the need for DPIA—does the personal information processing involve the information type specified in Article 55 of the PIPL?
- Describing the information flows—this can usually be combined with data mapping or ‘borrowing’ the output of the data flow mapping process
- Identifying privacy and related risks—what kind of risk is posed to individuals? For example, profiling, which is widely used, could lead to the individual paying higher prices to obtain the same service.
- Identifying and evaluating privacy solutions—can any Privacy Enhancement Technology (PET) be applied for better protection of personal information?
- Sign-off and recording the outcomes—the outcomes mentioned above need to be confirmed and recorded as the basis for the next phase of work
- Integrating the outcomes into a project plan—the outcomes of DPIA identify the existing issues, and the next step is to fix these problems
- Consulting with internal and external stakeholders—privacy involves lots of stakeholders, both inside and outside the organization, and good communication with all stakeholders will lead to earlier success in privacy management
Adoption of Privacy-related Technologies
As in the GDRP, the PIPL does not treat anonymized personal information as personal information. Therefore, a secure and effective way to eliminate the risks posed to personal information protection is making the personal information that a company possesses anonymous by using de-identification technology. Of course, this brings a further challenge to businesses, as many insights cannot be gleaned from the information once the data is anonymized. Striking a balance between the usability of personal information and the protection of said information is therefore a typical challenge that companies face.
The GB/T 37964-2019 Information Security Technology—Guide for De-Identifying Personal Information gives a more detailed introduction to de-identification. It also recommends a few commonly used technologies, such as statistics technology, suppression, encryption, generalization, and pseudonymization, to de-identify sensitive information, including names, ID numbers, bank account numbers, addresses, and phone numbers, among others. Determining which technology is the most suitable depends on various circumstances that may include the company’s budget and other needs.
Besides de-identification, PETs are also becoming increasingly popular. Differential Privacy is being applied by Apple for privacy protection in its iPhones, while Federated Learning and Secure Multi-Party Computation are used by banks for loan credit decisions and other purposes. However, the application of these PETs is often costly and therefore is mostly supplied by large market players, though some third-party service providers are emerging.
For small and medium-sized businesses, encryption would be an effective, low-cost solution to protect personal information. The most common options would be encryption of the Data at Rest, such as databases or files, to make sure data is unrecognizable even if a data leak happens and encrypting the network traffic with HTTPS to make sure the Data in Motion is well-protected.
Considerations for Cross-Border Data Transfer
If a company is identified as a critical information infrastructure (CII) operator, or the scale of personal data being processed reaches the limitations set by the Cyberspace Administration of China (CAC) as stipulated in the PIPL, and the data inside the company is identified as ‘core data’ or ‘important data’ as defined in the Data Security Law (DSL) of China, then the data should be saved within the territory of China and cannot be transferred outside of China, unless it passes a security review conducted by the CAC.
This data localization can create big challenges for companies, especially for their IT departments. It is common for MNCs to use a universal platform to serve all clients in different countries. Branch offices in China usually use IT systems built and hosted in the company’s headquarters, but this will inevitably lead to cross-border data transfer issues.
Companies that have standalone IT infrastructure in China to save related business data and personal information, might still need to further use the data in China for other business purposes, such as artificial intelligence-based analysis or big data analysis. The use of this data saved in a different location in China would be still considered cross–border data transfer. Moreover, allowing the other country’s staff to remotely access data saved in China over the internet would—in theory—also fall under the scope of cross-border data transfer, although we don’t believe this is currently a high compliance risk.
The good news is that the PIPL ‘borrows’ the concept of the Standard Contract Clause (SCC) from the GDPR, which allows companies to transfer personal information to overseas parties by signing a standard template agreement. Unfortunately, this template has not been published by the CAC yet. However, it provides a ray of hope for companies that can expect easier processes to be available in the future, compared to the significant efforts currently needed, such as conducting security reviews or receiving accreditation by an authorized agency, to transfer personal information outside of China.
Privacy by Design, Default
With the data localization requirements described above, we anticipate that some companies will consider deploying new standalone IT infrastructure in China to support their business as a way of meeting the compliance requirements. Several basic principles related to privacy, which were first introduced by Ann Cavoukian, the former information and privacy commissioner for the Canadian province of Ontario, should be considered when designing and deploying new IT infrastructure and systems:
- Proactive, not reactive; preventive, not remedial: In the software engineering industry, the cost of fixing a problem is always higher than preventing a problem from occurring in the first place. This can also be applied to privacy protection. The best strategy for privacy protection when designing the system or IT infrastructure is letting privacy drive the design, instead of allowing the design to dictate the privacy measures. When a privacy violation likely cannot be avoided, further actions need to be taken to remedy the issue, incurring high costs.
- Privacy as the default setting: When designing or configuring the systems or defining the internal data management process, privacy preservation should be the default setting. One common example of this is the choice offered when starting to collect personal data—should the data collection be opt-in or opt-out? The former gets an individual’s consent before collecting or processing personal data and lets the individual decide whether to allow his or her personal data to be processed. Opt-out just gives the option to withdraw consent after the personal data has been collected or processed. The opt-out method will be an obvious violation of any privacy law, including the GDPR and the PIPL. Similarly, some companies use CRMs to manage client contacts, for which there is usually a setting to control whether to allow the marketing team to send out promotional emails to contacts. This function should be turned off or set to “disallow” by default unless the operator is certain that sending emails is an appropriate action under the current circumstances.
- Privacy embedded into the design: This aspect may be particularly defined for the design of the software or IT system used for processing personal information. Like the design principle of “failure leads to safety” used for third-generation nuclear power plants, privacy should also be so ingrained into the design that the system or process would fail without the privacy-preserving functionality. The privacy team should be involved from the beginning of the project to analyze system or process requirements and work with the system architect, software engineer, developer, and operations team to define the privacy requirements at each stage of the process.
Organizational Control Measures
Finally, all the work described above must be done by personnel, either by internal teams or outsourced to an external team. Hiring a privacy team with qualified privacy expertise, which usually combines both legal and technology experts, is the top priority for a company when starting to deal with compliance risks. Companies that don’t have a legal entity in China but provide services or products to people in China, or data processors who handle large amounts of personal information, are required by the PIPL to appoint specific personnel to oversee personal information protection. This is like the data protection officer (DPO) required under the GDPR. For small and medium-sized businesses that lack adequate internal resources, seeking a professional agency to play that role is a suitable option.
Meanwhile, the company should consider creating effective processes for managing all work related to personal information protection, with well-defined and clear policies, procedures, and guidelines. Privacy awareness training is necessary to make sure all staff are aware of the importance of personal information protection to the business, clients, other third parties, and themselves. The employee should also recognize personal information and must know what actions to take when processing personal information.
This article was first published by China Briefing, which is produced by Dezan Shira & Associates. The firm assists foreign investors throughout Asia from offices across the world, including in China, Hong Kong, Vietnam, Singapore, India, and Russia. Readers may write to [email protected] for more support.